Part 1:
Why am I writing this:
- The documentation is vague and all over the place. Much of it is for Linux based OSes.
- The certificate-store-path variable in the plugin properties does not work, so that part of the documentation is wrong, and the trick is to put the keystore on the C: root.
- It's not obvious to a non-PGP user how to set multiple users or a group of users as "admin."
- Answers are hard to find, so my goal is to limit the trial-and-error approach
Overview:
- Symantec DLP (Data Loss Prevention) discovers data that may be deemed sensitive or important based on policies created by an organization.
- PGP encrypts data
- It is possible to integrate the two products so that incidents generated by DLP can be then used to encrypt the file(s) in question.
In this scenario there are three servers: PGP Universal Server/Symantec Encryption Management Server (v.2.3.0) (SEMS), ERM (Enterprise Rights Management) Server, and DLP Enforce (v.12.0.1) (front end).
ERM Server:
Prerequisites: Windows Server 2003 SP2/2008 (x84/x64) (not R2)The ERM service account user must be:
- An AD domain acct
- Be able to login to the ERM server host computer.
- Be enrolled with PGP NetShare and have a key-pair resident in its local key-ring.
- Be granted read/write access to the file-shares on which files are to be encrypted. This is required only for NetShare, due to limitations of the PGP NetShare command-line.
DLP Enforce Server:
Prerequisites: DLP v.10+PGP/SEMS:
PGP Desktop/PGPNetshare v.9.12+For group lookup, the PGP Desktop must be bound to a PGP universal server v.2.12+.
And a general description of how PGP works.
An organization wants to encrypt files/folders/shares. This will render those "files" useless to anyone who does not have the key and decryption software. The trouble with single keys is that they can be lost easily or passwords can be forgotten. Even if the keys are not lost, having only one user do the management of the decryption/encryption process would be unwieldy. An encryption server hosts all keys for an organization, provides a single place to go to set/get keys/users/devices, and can enforce use of a backup key and/or a group of users who have the ability to manage encryption for the organization.PGP encryption has three levels of encryption users: Admin, Group Admin, and User. The Admin user/group can decrypt/encrypt and assign permissions to all levels, and there can only be one (Highlander!). A Group Admin can assign permissions to other Group Admins and Users. A User can read the encrypted file.
Encrypted files on a computer without encryption software will appear corrupt or inaccessible because the computer has no way of understanding how to read the file.
However, opening an encrypted file on a computer with encryption software will either allow access transparently (the file will be automatically decrypted and opened after the PGP passphrase is entered once (and cached for session)), or there will be some sort of "access denied" message. There will also be a new tab on the file properties called "PGP Netshare" to view and edit the encryption access permissions similar to the windows file security tab.
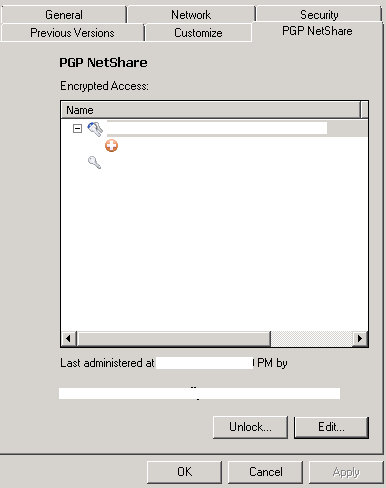 |
| PGP Netshare file properties tab |
And there will be a context menu that allows a file to be encrypted, re-encrypted, or decrypted.
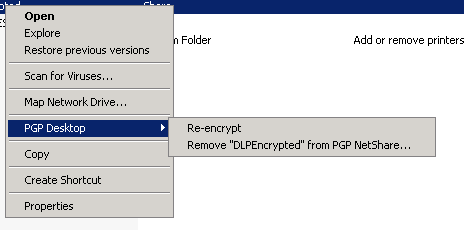 |
| PGP Desktop file context menu |
The goal is to allow objects to be secured without infringing upon the user's ability to work. The way this all comes together is through encryption groups that are managed by the PGP Universal server. When user with a key and the correct software takes sensitive data off-site, they can still open that file. If the encryption access is setup using groups, the user's device will require a connection to the organization's PGP server to verify that the current user exists and has access to the file. This adds a lot of security. So what we want the DLP integration to do is:
- Encrypt files
- Talk to the PGP Universal server
- Set Admin permissions to a group of users
- Set User permissions to a group of users
Step 1 - Configure a DLP related encryption group on the PGP Universal Server
On the PGP Universal Server (web interface):
Go to Consumers (tab)-Groups and setup an administration group for your encrypted files (maybe call it "DLP_Admins"). Users in this group will be able to decrypt and manage the access for encrypted files and folders.Then go to Keys (tab)-Managed Keys. Click on the group name you setup as your administration group. Click Export-Export key-pair, and enter a passphrase. **Document this passphrase for later**. Save this export as a file. It contains the private and public key-pair for the group.
Step 2 - Install PGP Desktop and Import Key From Step 1
On the ERM Service host server:
Install PGP Desktop on the ERM Service host computer (This will require a reboot.)
Enroll the ERM service account on the PGP Universal server. The enrollment process should be initiated automatically after the reboot. Depending on your PGP configuration it may require an AD account, an email address, or potentially even a silent enrollment. It is also possible that the ERM service account was enrolled in the past and a key may already exist for this account.
You must have a local keyring for this service account that is not SKM key mode. SKM key mode does not allow for a known keyring passphrase.
If your service account has an SKM key:
Look at the account's key type in the Universal server.
Open PGP desktop, go to Tools(menu) - Options - Advanced(tab). Click "Reset Key", choose SCKM, enter the a passphrase (*the same one used when exporting the administration group key-pair*), and complete.
Still in PGP Desktop on the ERM host machine, go to File-Import, select the administration group key file, and click "Import." In your keyring (PGP Keys(tab)-All Keys) you'll see this administration group. Double-click the group name and choose "Implicit" under the "trust" selector. Because you imported the keypair containing both the public and private keys you can now sign encryption using this group's key. Any user in this PGP group will be able to administer a file encrypted by this service.
Step 3 - Install and Configure ERM Service
Extract the ERMService files by running the PGP Plugin exe:
This will be found in the DLP Platform installs folder: Symantec_DLP_12.0_Platform_Win-IN\DLP\12.0\FlexResponse_Plugins\PGP\Symantec_DLP_Plugin_PGP_1.0.2.0.exe
Install the ERMService.MSI (this is the middle-man between DLP and PGP/SES)
**This can be installed on the DLP Enforce server if it meets the prerequisites (pre-server 2008 R2).
Configure the service by editing the xml file here:
C:\Program Files (x86)\Symantec\DLP ERM Service\sdlperm-config.xml (location will vary depending on OS)
You'll have to copy the file elsewhere to edit it and then copy it back.
In the <web-services> section enable the REST web interface
<enabled>true</enabled>
In the same section make sure SSL is enabled if the ERM service is not installed on the DLP Enforce server.
In the <pgp-netshare-config> section, set <enabled> to true, and make sure the cmdline-path points to the installed location of PGP Desktop.
<cmdline-path>C:\Program Files (x86)\PGP Corporation\PGP Desktop\pgpnetshare.exe</cmdline-path> (location will vary depending on OS)
Fill in the signer you will use (the keyid of the administration group in keyring).
<signer>0x########</signer>
Put the keyring/group export passphrase here.
<passphrase></passphrase>
You will remove this passphrase later on because leaving it here in plaintext is insecure.
You could use the service account key/username as the signer as well, but know that the signer becomes the "Admin" of the encryption and will be the only user who can decrypt or edit access to the encrypted object. This would be a management/workflow hassle and you don't want to use a service account for this, so it's better to have a group do this.
The following is optional:
Now edit this file: C:\Users\<accountname>\AppData\Roaming\PGP Corporation\PGP\PGPprefs.xml (location will vary depending on OS)
Search and find "<key>useAlwaysEncryptToKeys</key>"
This key holds an array of implicit user keys to add to any encryption. This is useful if there are some users or groups (like the "Everyone" group in PGP Universal server) who should be always able to read an encrypted object.
Add additional keys as needed. i.e. <string>0x#######1</string><string>0x#######2</string>
You can also search for "<key>ADKKeyID</key>" and put in your organization's alternate decryption key into the field. I.e. <key>ADKKeyID</key><string>0x########</string>
Then restart the ERM service "Symantec Data Loss Prevention ERM Service"
This completes the setup of the ERM Service. Part 2 will focus on setting up the DLP Plugin.